Secure Elasticsearch without X-Pack or SSL/TLS
HowTo Secure Elasticsearch using spiped on FreeBSD, Debian and CentOS
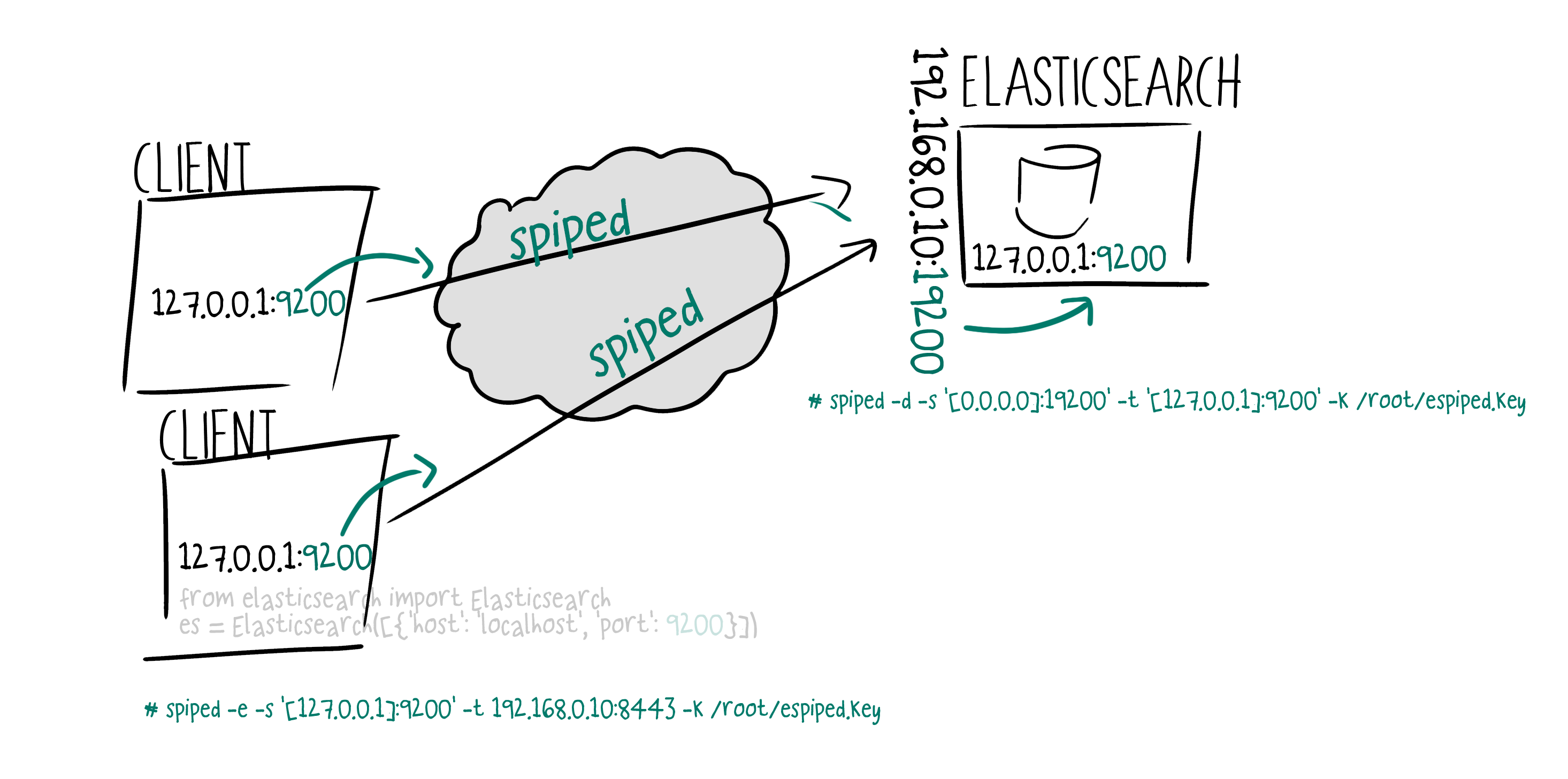
Spiped makes it really easy to secure connections between clients and Elasticsearch databases.
 Keep in mind that the symmetric key (once compromised) can be used to intercept/mitm all connections.
Keep in mind that the symmetric key (once compromised) can be used to intercept/mitm all connections.
install spiped
FreeBSD
pkg install spiped
Debian/Ubuntu
apt install spiped
CentOS
vim /etc/yum.repos.d/spiped.repo
[lsde-spiped]
name=Copr repo for spiped owned by lsde
baseurl=https://copr-be.cloud.fedoraproject.org/results/lsde/spiped/> epel-7-$basearch/
type=rpm-md
skip_if_unavailable=True
gpgcheck=1
gpgkey=https://copr-be.cloud.fedoraproject.org/results/lsde/spiped/pubkey.gpg
repo_gpgcheck=0
enabled=1
enabled_metadata=1
install spiped
yum clean all
yum install spiped
generate symmetric encryption key
dd if=/dev/urandom of=/root/espiped.key bs=32 count=1
and copy the key file onto every client (rsync, scp, whatever…)
run spiped on Elasticsearch database server (you should know how to configure your firewall)
Spiped will listen on port 19200 and forward traffic to 9200 (TCP forwarding must be enabled)
spiped -d -s '[0.0.0.0]:19200' -t '[127.0.0.1]:9200' -k /root/espiped.key
run spiped on client Spiped will listen on port 9200 and forward to the Elasticsearch DBS port 19200
spiped -e -s '[127.0.0.1]:9200' -t 192.168.0.10:19200 -k /root/espiped.key