How to create secure remote access with zero trust policy
How to create secure remote access with zero trust policy
This short how-to should give you some ideas on how to create secure web access to your web services without VPN.
First of all: You can stop reading (and probably using Internet after all) if you don’t trust any content providers. I will use Cloudflare, OPNsense, Solokeys and Github for this Demo. You need a fixed IP-address or just use Cloudflare’s DynDNS service as well.
This is not a complete step-by-step guide! You should know what you’re doing before exposing confidential/private services on the internet.
Register your TLD with Cloudflare’s NS servers
First you need to transfer one TLD (NS servers to be precise) to Cloudflare. It’s pretty straight forward and there are plenty of how-tos, so I’ll just skip it.
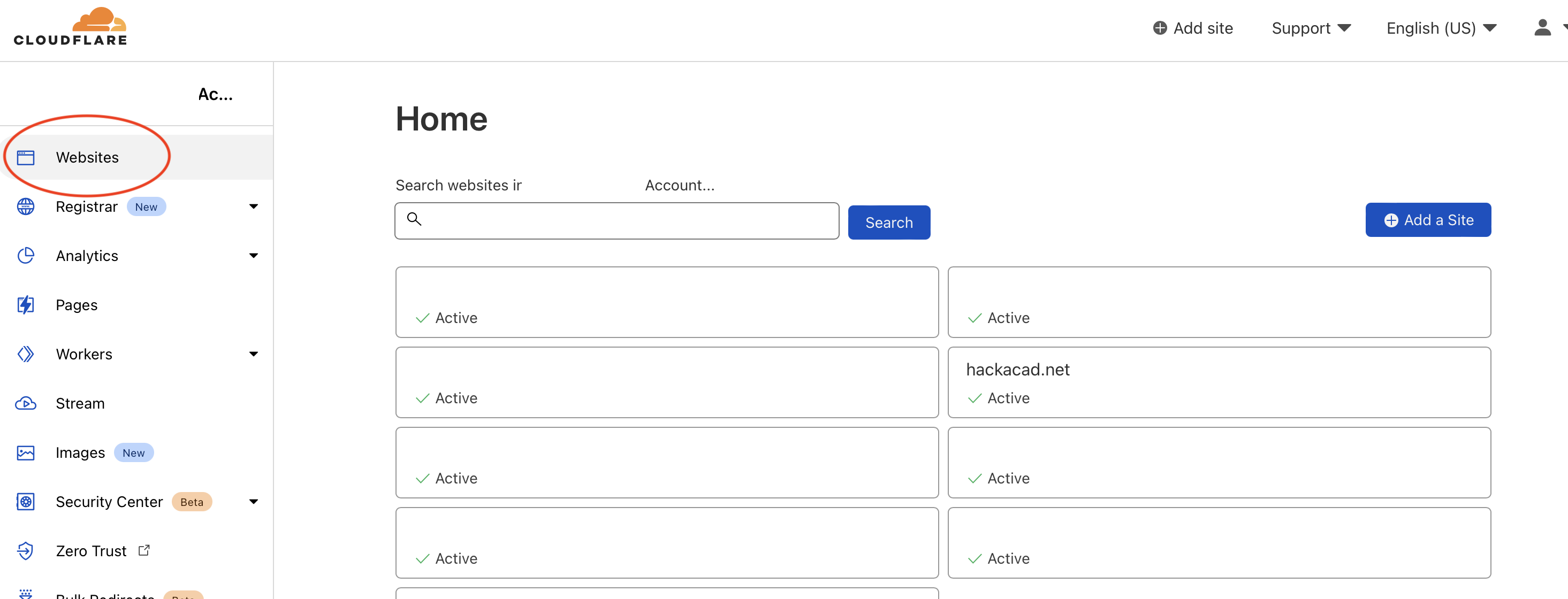
Set up the Web Application Firewall
Once you moved your domain, you can set up a WAF. This should block many scanners and internet noise, unless you chose to allow common hosting providers.
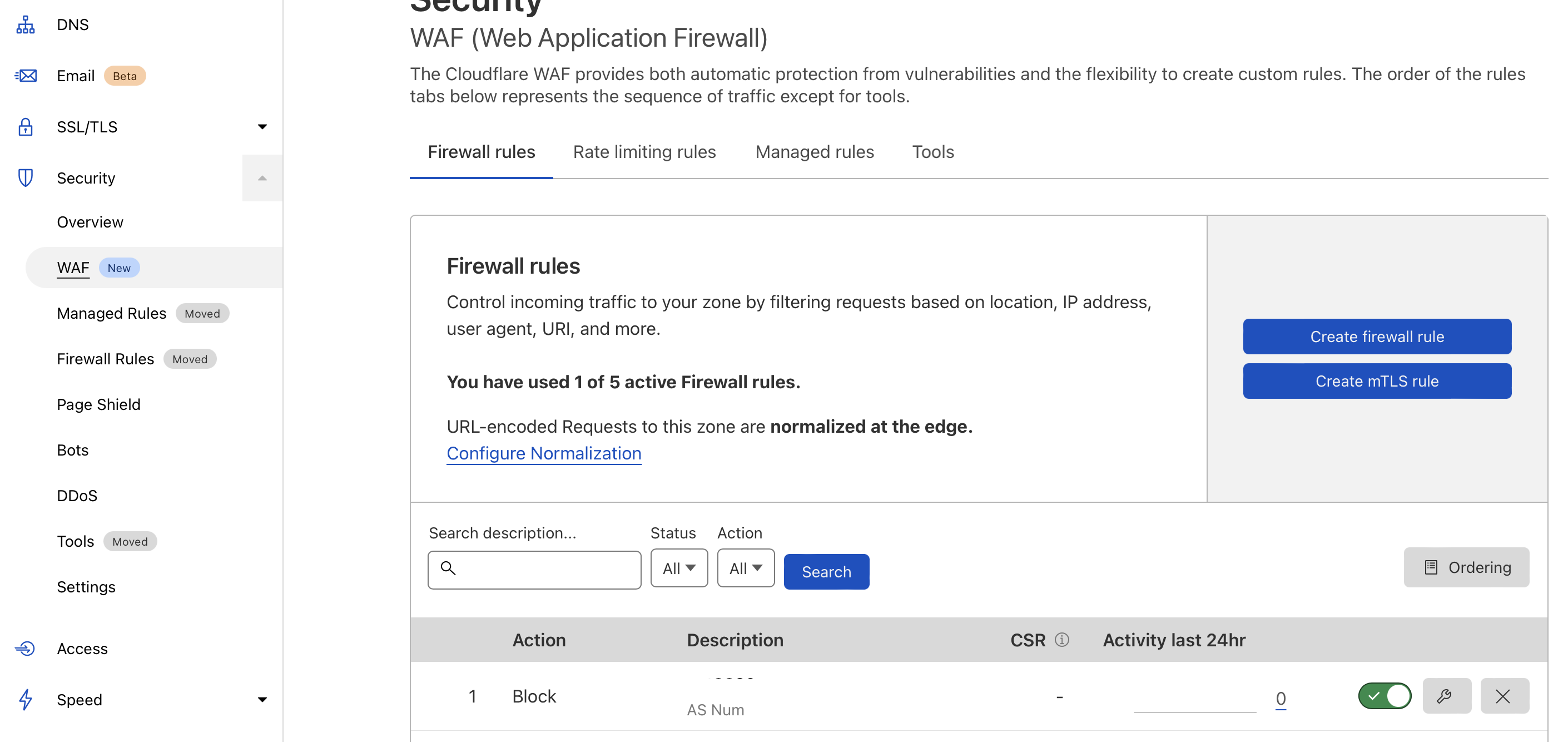
Create a Zero Trust App Access
Next go to Zero Trust -> Access -> Add new Application Give it a name and select a subdomain
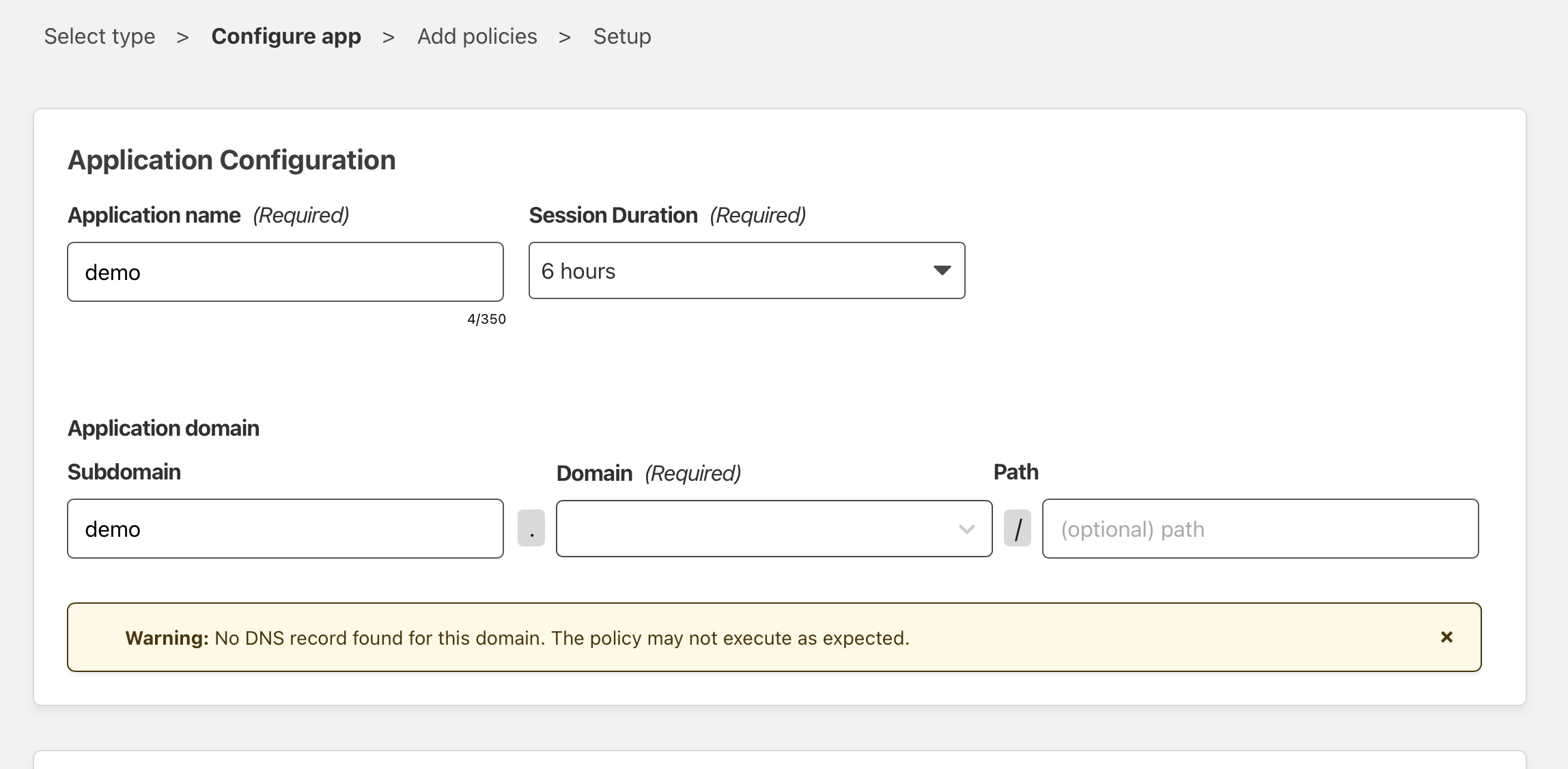
Add an identity provider (Github, TOTP, Facebook, …)
You need to add at least one identity provider. I like Github because it offers FIDO2 2FA, so I can use my Solokeys as second factor.
 Add the email addresses or IDs you want to use for authentication.
Add the email addresses or IDs you want to use for authentication.
Create a proxied A record
Go back to your domain manager and create a proxied A record from the subdomain you choose before.
Set up your host or firewall for dedicated remote access
At last, you need to configure your firewall to block any access except Cloudflare traffic. This can be done easily using FreeBSD pf tables or OPNsense aliases.
Login to your OPNsense (or create a file on your FreeBSD host) and add all (Cloudflare IP addresses)[https://www.cloudflare.com/ips/].
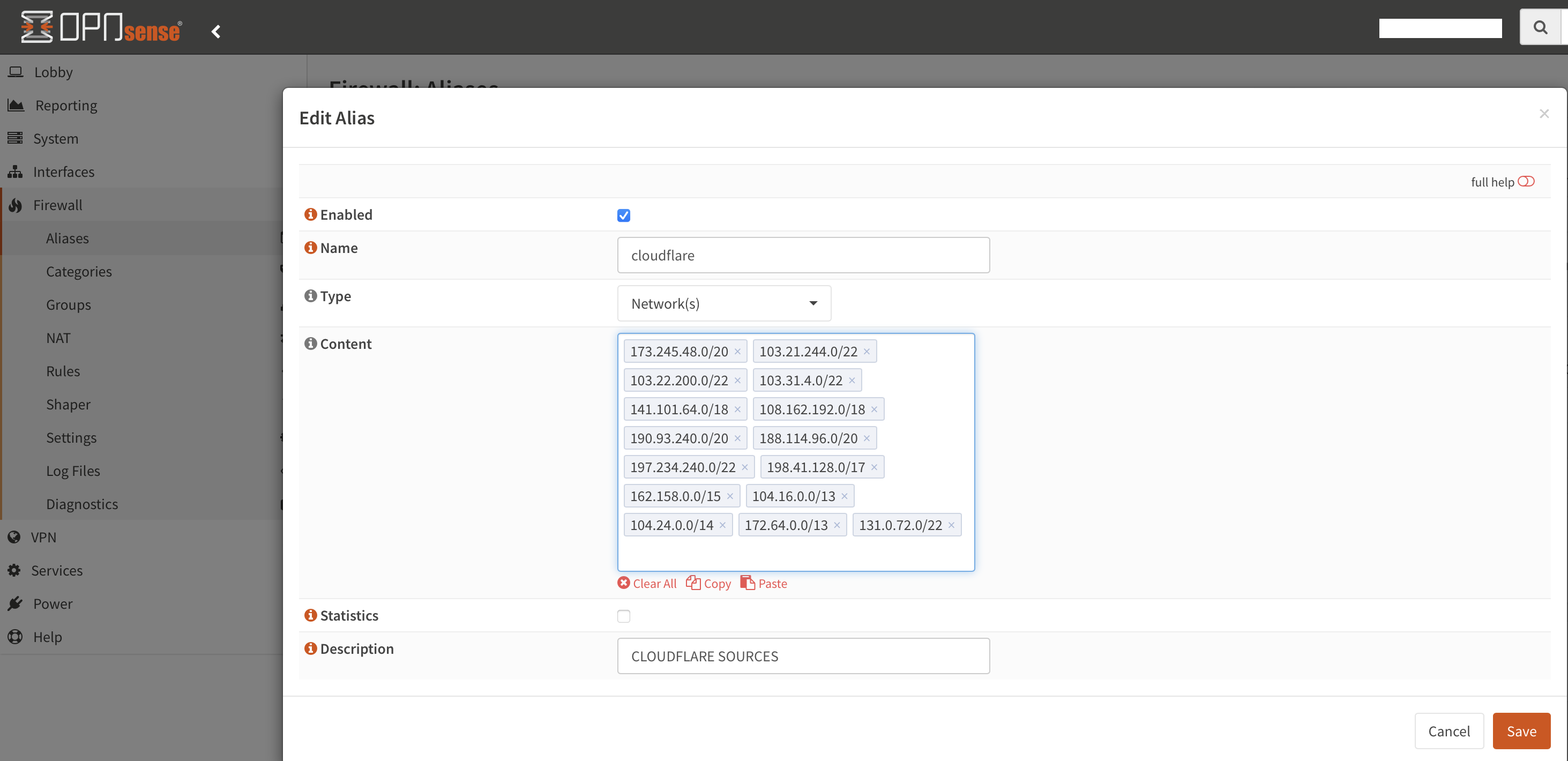 (for FreeBSD hosts it’s just normal
(for FreeBSD hosts it’s just normal pf tables persist <conf/cloudflare> + pass in from table <cloudflare>
Add a rule to forward traffic to your web server, and you’re done doing the basic configuration.
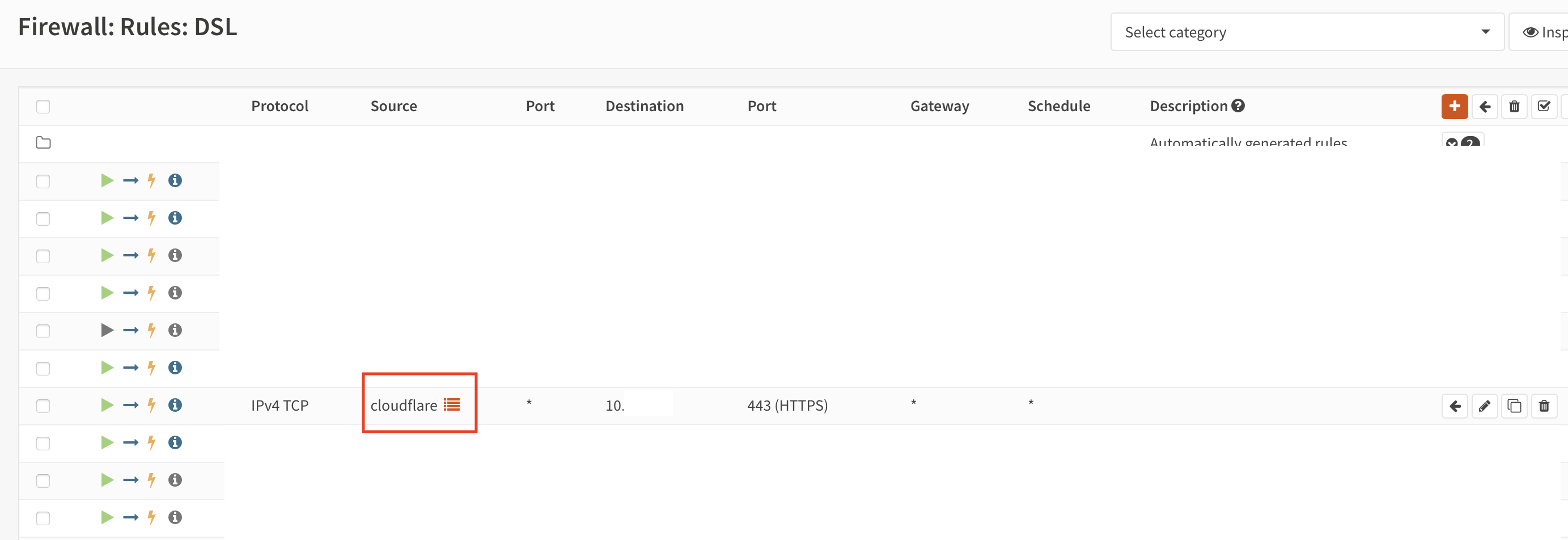
To add more security you should use client certificates (mTLS). See you next time…