How to secure your Saltstack Salt Master using spiped
This is a short how-to for securing Saltstack communication via spiped.
(most of it is based on the how-to I wrote on securing Elasticsearch with spiped)
At first: install spiped
FreeBSD
pkg install spiped
Debian/Ubuntu
apt install spiped
CentOS (fo those who haven’t migrated yet)
vim /etc/yum.repos.d/spiped.repo
[lsde-spiped]
name=spiped repo
baseurl=https://copr-be.cloud.fedoraproject.org/results/lsde/spiped/epel-7-$basearch/
type=rpm-md
skip_if_unavailable=True
gpgcheck=1
gpgkey=https://copr-be.cloud.fedoraproject.org/results/lsde/spiped/pubkey.gpg
repo_gpgcheck=0
enabled=1
enabled_metadata=1
install spiped
yum clean all
yum install spiped
generate symmetric encryption key
dd if=/dev/urandom of=/root/saltpipe.key bs=32 count=1
and copy the key file onto every client
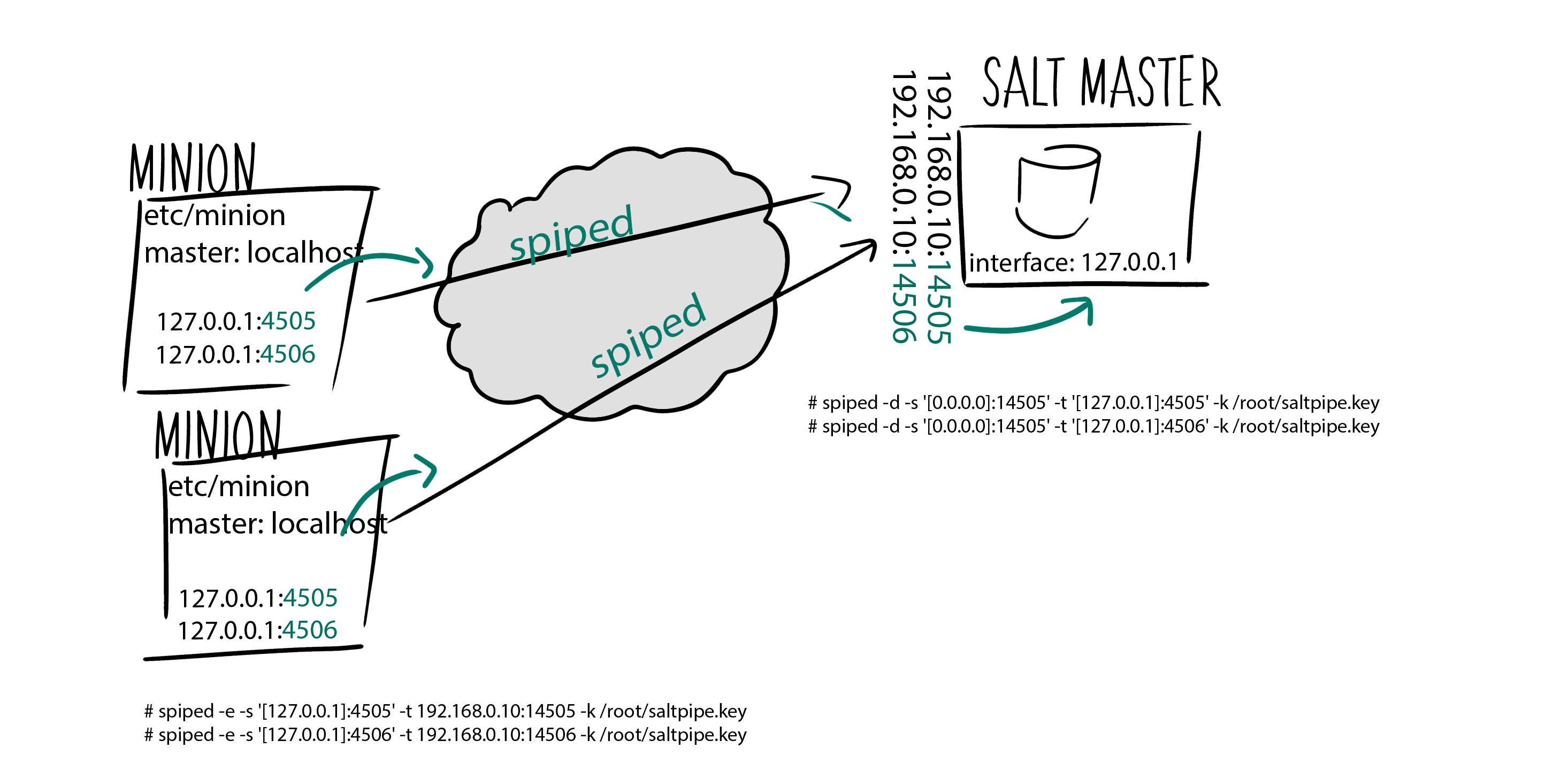
run spiped on Salt MASTER
Spiped will listen on port 14505/14506 and forward traffic to 4505/4506 (TCP forwarding must be enabled)
spiped -d -s '[0.0.0.0]:14505' -t '[127.0.0.1]:4505' -k /root/saltpipe.key
spiped -d -s '[0.0.0.0]:14506' -t '[127.0.0.1]:4506' -k /root/saltpipe.key
run spiped on Salt MINION
Spiped will listen on port 4505/4506 and forward to the Salt master on ports 14505/14506
spiped -e -s '[127.0.0.1]:4505' -t 192.168.0.10:14505 -k /root/saltpipe.key
spiped -e -s '[127.0.0.1]:4506' -t 192.168.0.10:14506 -k /root/saltpipe.key
Now automate that by adding it to systemd:
on Salt MASTER
vim /etc/systemd/system/spiped-4505.service
(don’t forget -F)
[Unit]
Description=spiped receive Saltstack 4505
Wants=network-online.target
After=network-online.target
[Service]
ExecStart=/usr/bin/spiped -F -d -s [0.0.0.0]:14505 -t 127.0.0.1:4505 -k /root/saltpipe.key
[Install]
WantedBy=multi-user.target
vim /etc/systemd/system/spiped-4505.service
[Unit]
Description=spiped receive Saltstack 4506
Wants=network-online.target
After=network-online.target
[Service]
ExecStart=/usr/bin/spiped -F -d -s [0.0.0.0]:14506 -t 127.0.0.1:4506 -k /root/saltpipe.key
[Install]
WantedBy=multi-user.target
vim /etc/salt/master
interface: 127.0.0.1
and enable/start all services
systemctl enable spiped-4505
systemctl enable spiped-4506
systemctl start spiped-4505
systemctl start spiped-4506
systemctl restart salt-master
If you’re running FreeBSD you can simply add the startup commands to /etc/rc.conf and run
sysrc spiped_enable=YES
service spiped start
vim /etc/rc.conf
spiped_pipes="publish returner"
spiped_pipe_publish_mode="decrypt" #use client on minion
piped_pipe_publish_source="[0.0.0.0]:14505"
spiped_pipe_publish_target="127.0.0.1:4505"
spiped_pipe_publish_key="/root/saltpipe.key" #or any key you created
spiped_pipe_returner_mode="decrypt" #use client on minion
spiped_pipe_returner_source="[0.0.0.0]:4446"
spiped_pipe_returner_target="10.0.0.1:4506"
spiped_pipe_returner_key="/root/saltpipe.key" #or any key you created
on Salt MINION
vim /etc/systemd/system/spiped-4505.service
(don’t forget -F)
[Unit]
Description=spiped transmitter Saltstack 4505
Wants=network-online.target
After=network-online.target
[Service]
ExecStart=/usr/bin/spiped -F -e -s [0.0.0.0]:4505 -t 192.168.0.10:14505 -k /root/espiped.key
[Install]
WantedBy=multi-user.target
vim /etc/systemd/system/spiped-4506.service
[Unit]
Description=spiped transmitter Saltstack 4506
Wants=network-online.target
After=network-online.target
[Service]
ExecStart=/usr/bin/spiped -F -e -s [0.0.0.0]:4506 -t 192.168.0.10:14506 -k /root/espiped.key
[Install]
WantedBy=multi-user.target
vim /etc/salt/minion
master: localhost
and enable/start all services
systemctl enable spiped-4505
systemctl enable spiped-4506
systemctl start spiped-4505
systemctl start spiped-4506
systemctl restart salt-minion